Network:
Data can be exchanged between computers through various means, including direct cable connections, wireless technologies, fiber-optic cables, modems, and satellite communication. Traditionally, telephone lines and dial-up modems were used for data transmission, but today, optical fiber, broadband connections, mobile networks (3G, 4G, 5G), and Wi-Fi have become the primary mediums due to their speed and reliability. An effective network infrastructure relies on both hardware (such as routers, switches, servers, and access points) and software (including network operating systems, protocols, and security tools).
A computer network is a system that interconnects multiple computers and devices to share information, data, and resources. The number of devices that can be connected to a network is virtually unlimited, depending on its design and infrastructure.
– When computers are connected within a limited area—such as a school, office, or building—the network is referred to as a Local Area Network (LAN).
– When a network extends across a broader geographical region, such as between cities or countries, it is called a Wide Area Network (WAN). The internet itself is the largest example of a WAN.
At the core of most networks is a server, a powerful computer that manages resources, user access, and data exchange among client computers. Modern networks may also utilize cloud servers, which provide storage, applications, and services over the internet.
Through computer networks, users can share files, access shared hardware (like printers), communicate instantly, collaborate on projects, and connect to global resources. Networks have become the backbone of communication, education, commerce, and nearly every sector of modern life.
Network topology
Network topology refers to the arrangement and relationship between two or more computers within a network. This arrangement directly impacts the reliability and efficiency of the network. Topology provides a clear overview of the network’s structure, showing the locations of different computers and how they connect to one another.
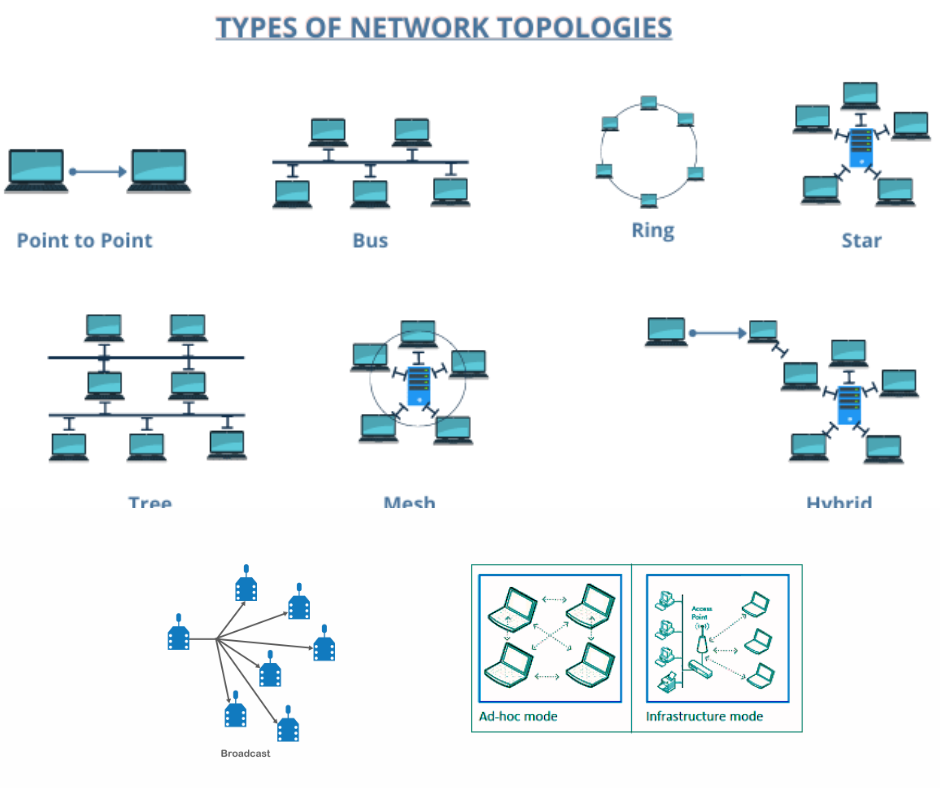
There are generally four types of network topologies.
- Bus Topology: In this type, all computers are connected via a single cable known as the bus. When one computer sends out a message, it is transmitted to all other computers on the network. Each computer receives this signal and decides whether the message is intended for it. Bus topology is commonly used in local area networks (LANs). An advantage of this setup is that the failure of one computer does not cause the entire system to collapse. Additionally, new computers can be easily connected or disconnected from the network at any time.
- Star Topology: A star topology consists of a network connected through a central computer known as the server. In this setup, all messages and information pass through the server. When one computer wants to send a message to another, it first sends the message to the server. The server then forwards the message to the intended recipient computer.
One major drawback of this system is that if the server fails, the entire network becomes inoperable and the connection is lost. However, when the server establishes a connection between two computers, the dedicated connection allows for very fast transmission of data.
3. Ring Topology: In a ring topology, computers or nodes are interconnected in a circular fashion. In this system, each computer can communicate with others by sending signals along the entire loop. Each node has a specific address associated with it. When a message is sent to a particular destination, it travels around the circular path, and each node checks whether the message is intended for it. If it is not, the node passes the message along to the next one in the ring.
This topology is somewhat similar to a bus topology; however, in a ring topology, all nodes are connected to each other, playing a direct role in the communication process. One major disadvantage of this system is that if one node fails, it can significantly disrupt part of the network, although the remaining nodes will continue to function. Additionally, making changes to the network is more complex in this topology.
4. Hybrid topology : Hybrid topology is a network configuration that integrates elements from both bus and star topologies, allowing it to leverage the advantages of both systems. In a hybrid topology, multiple star networks can be interconnected through a bus structure, or various bus segments can be arranged in a star formation. This versatility makes hybrid topology particularly suitable for large-scale networks that require scalability and flexibility.
By combining these two topological structures, hybrid networks can efficiently manage a significant number of devices while ensuring robust performance and reliability. For instance, if one segment of the network experiences failure, it does not necessarily disrupt the entire system, which enhances fault tolerance. Additionally, hybrid topologies can be easily expanded by adding new devices or additional network segments without major overhauls, making them ideal for enterprise environments with evolving connectivity needs.
These networking topologies are still considered fundamental in the field, but modern networking has introduced a few additional topologies that are widely used, especially as networks have become larger, more complex, and increasingly internet-centric.
The modern networking Topology
- Mesh Topology :
Mesh Topology connects every device to every other device, either fully (full mesh) or partially (partial mesh). This topology is highly reliable because there is no single point of failure; if one connection breaks, data can be rerouted through alternative paths. This makes mesh topology particularly useful in large-scale networks, military systems, and the internet backbone, where redundancy and fault tolerance are critical. However, its major drawbacks are cost and complexity. Implementing a full mesh requires numerous connections and becomes increasingly expensive and difficult to manage as the network expands.
2. Tree Topology (Hierarchical Topology) :
Tree Topology (Hierarchical Topology) combines elements of both star and bus topologies, forming a hierarchical structure. In this setup, a central root node connects to sub-nodes that branch out in layers. Tree topology is highly scalable, making it suitable for large organizations with multiple departments, and its structured layout enhances management and troubleshooting. However, a significant drawback is its vulnerability to root node failure, which can disrupt large portions of the network.
3. Point-to-Point Topology :
Point-to-Point Topology is the simplest form of networking, where exactly two devices are connected directly through a dedicated link. This setup provides fast and reliable communication, making it ideal for applications like leased lines, direct microwave, or satellite links. However, its biggest limitation is scalability; it cannot support more than two devices, making it unsuitable for larger or more complex networks.
4. Point-to-Multipoint Topology :
Poin-to-Multipoint Topology refers to a network configuration where a single central device communicates with multiple connected devices. This topology is commonly used in wireless networks, cellular towers, and satellite communication systems due to its efficiency in serving many users from one source. However, its major drawback is heavy dependency on the central node; if it fails, communication for all connected devices is disrupted, making the reliability of the central device crucial for smooth operation.
5. Wireless Topologies (Ad Hoc & Infrastructure)
Wireless Networks can be classified into two main types: ad hoc, where devices connect directly to each other without using a central router, and infrastructure, where devices communicate through access points such as Wi-Fi routers. These networks offer significant advantages, particularly in terms of flexibility and mobility, making them ideal for dynamic environments where quick and easy connections are needed. However, a major disadvantage is security; wireless connections can be vulnerable to unauthorized access and attacks if not properly protected with strong encryption and authentication measures.
In conclusion, understanding different network topologies and their strengths and weaknesses is essential for designing reliable, scalable, and secure communication systems that meet the diverse needs of modern life.